The internet is not as secure a place as we all wish it was. Without the proper security, it’s far too easy for hackers to steal credit card information and other details. So how do website owners protect visitors’ personal information? With SSL, or Secure Sockets Layer.
In this post, we’ll help business owners and website managers understand what SSL is, how it works, and how you can put it to good use on any website.
What is SSL?
We’ve all seen signs of SSL technology in the URL bar. If you’ve ever noticed that some URLs begin with “http://” but others begin with “https://,” you’ve seen it at work. SSL is security tech that uses various techniques to keep data sent between web servers and browsers safe. And that’s why it’s so important for websites, especially those with eCommerce elements.
Why Ecommerce Needs SSL
SSL is used on website pages where personal or confidential information can be typed in. Ecommerce sites are perfect examples of this. Think of how much personal data customers type in while ordering something online – credit card numbers, home addresses, etc.
Using Bed Bath & Beyond’s website as an example, we can see that the homepage is not secure (because there is no “https://” included at the front of the URL). But it doesn’t need to be because no one is inputting information on this page.
If we add a product to our shopping cart and then view the cart page, it’s still not secure. But what happens when we go one step further?
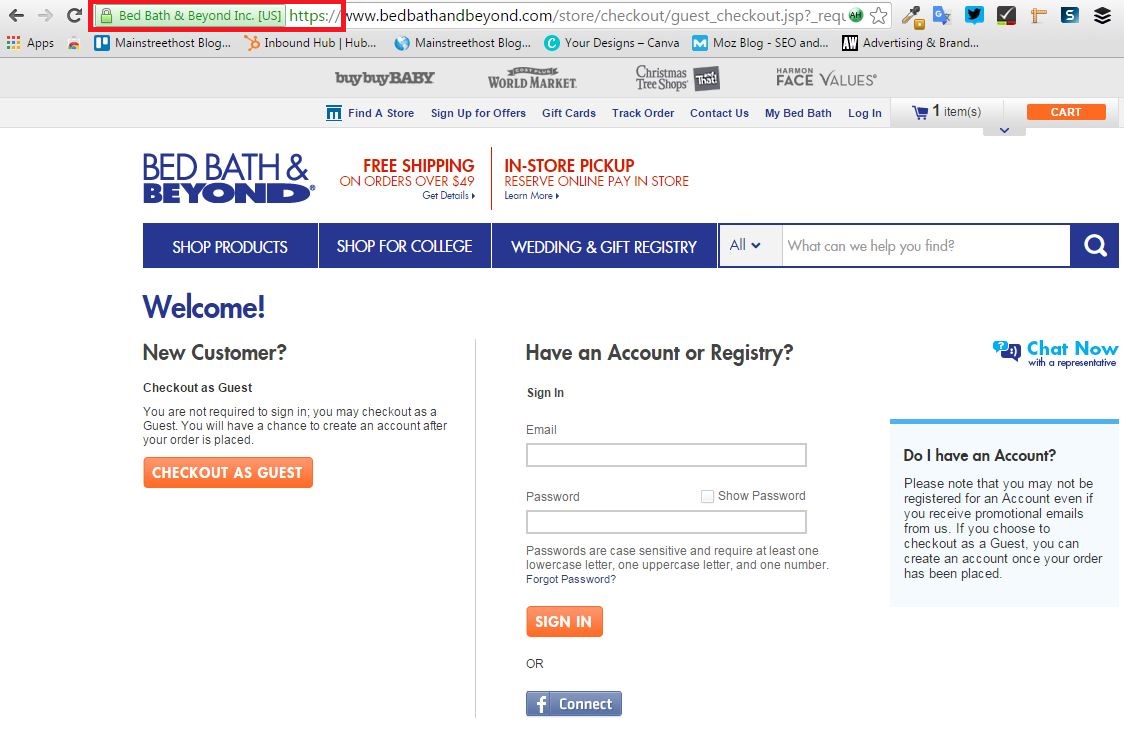
After clicking the “proceed to checkout” CTA, the little green lock icon and “https://” in the URL show us that this page is secure. People trust stores like Bed Bath & Beyond to protect their information from hackers during the online shopping experience. With these markers in the URL, BB&B’s customers can shop with confidence.
But Why is All of This Necessary? How Do Hackers Get Ahold of Private Information?
Hackers install listening programs on pages where visitors need to type in information (like the page above). These programs are usually undetectable and will wait patiently until someone comes along and starts typing. The program then intercepts the info and relays it to the hacker. Of course, this means that eCommerce websites should never just store customer credit card details without the proper precautions (making sure you’re PCI compliant). As ReQtest colorfully puts it, “Besides making your site a low-hanging fruit with huge rewards for criminals, you’re also losing business every time a user realizes you do this and closes the tab in disgust.”
Not having that lock symbol and an “s” accompanying “http” in your URL is a huge warning to potential customers: “Beware of putting your private information on our website because we have no way of stopping people from stealing it.”
How Does SSL Protect Your Website?
SSL protects data by setting up a secure link between the web server and the customer’s browser. Any information inputted by the customer on his or her end will be encrypted while transmitting across the link to the web server. Information sent across a secure link is safe because reading encrypted data requires a key or password (more on this in the following section).
Encryption is what happens to text that is submitted by the customer. Their computers automatically translate what they’ve submitted into ciphertext (again, keep reading). Once received, the host’s server decrypts this ciphertext information back into text that can be read and understood.
The Difference Between Asymmetric vs. Symmetric Encryption
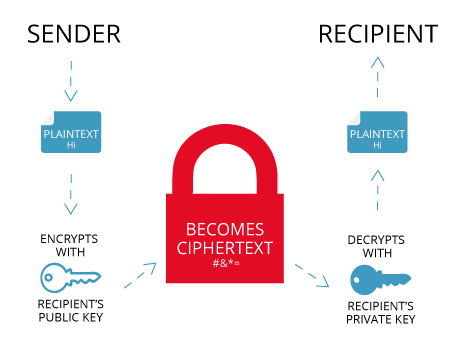
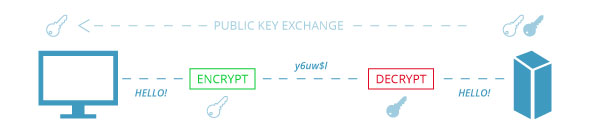
Encryption and decryption would not be possible without keys. Just like with the physical versions, these digital keys are used to lock and unlock. With asymmetric encryption (also called public-key encryption), the total transfer of information uses two different keys – one for encrypting the information and one for decrypting (the use of two keys is why asymmetric is the safer encryption mode).
The encryption key is also known as the public key and can be used by anyone (like someone purchasing an item online). All they have to do is enter information on an SSL-secured site. Customers don’t even know this process is happening behind the scenes while they complete their purchase.
The information submitted by the customer is inputted as plaintext (regular words and sentences) because that’s how we type and read. The public key takes that plaintext and encrypts it into ciphertext – making it impossible to read. Here’s where asymmetric encryption’s two different keys come in. The second key, or the private key, is secret and is only known by the intended recipient of the original information. The recipient (a business like Bed Bath & Beyond, for example) uses the private key to decrypt the ciphertext back into plaintext.
In the following images, the light keys represents the public key while the dark keys represents the private one.
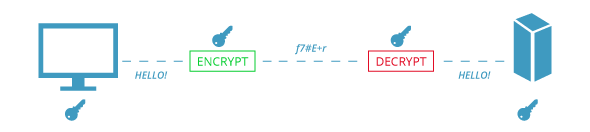
Symmetric encryption (also referred to as shared or secret-key encryption), on the other hand, uses the same key to both encrypt and decrypt info. This is what makes asymmetric encryption the more secure of the two options. With symmetric, the public key has to be guarded against potential hacking because it’s the access to both locking and unlocking the information being sent. Alternatively, it doesn’t matter who has the public key for asymmetric encryption because only the person with the private key can decrypt the information.
Certificates
All websites can be secured with SSL – there are just a few steps to complete first.
- Decide which type of SSL you should get based on your individual needs using DigiCert’s resource.
- Certificate Signing Requests (CSRs) must be generated by applicants requesting an SSL Certificate. And all sites that want to use SSL must obtain a certificate. This is the first step towards getting one, and information like domain name, organization, city, state, country, country code, etc. is required. Generating these requests typically takes some background knowledge of web server software, but Comodo’s step-by-step documentation can help anyone create CSRs on the most common types of software. After completing the steps, CSR requestors should have the actual CSR as a block of text with “Begin Certificate Request” before and “End Certificate Request” after.
- After the CSR has been generated, it’s time to order a certificate from a recognized authority like Comodo or DigiCert. If your website is hosted on GoDaddy or HostGator, you can purchase your SSL Certificate directly through them. If you use HubSpot’s website platform, SSL is completely free! At the end of the process, there should be an option like “Go to Next Steps.” This is the page where the CSR block of text generated earlier will be entered and submitted.
- The certificate authority will then verify the information submitted, making sure the web domains and personal information are all accurate. If everything checks out, a certificate will be issued.
- After all of the information is verified, the certificate can then be installed on the site’s web server. Different severs have different installation processes, so Comodo has once again written detailed documents to walk us through it.
- The web server will then create the public and private keys mentioned earlier and set up a secure, encrypted connection between the website and potential customers’ browsers. Because these certificate authorities use asymmetric encryption, the private key will be discreetly issued to the host server or business/website owner. And as a result – even the certificate authority that created the key will not know what it is.
If you want to learn more about how these keys are created, click the link here to read DigiCert’s explanation of the algorithms behind the process.
How Can You Tell if SSL is Installed?
As we mentioned earlier, there are a few ways you can make sure SSL is on a website. The lock symbol in the left-hand corner of the URL bar has become an iconic symbol for web security. The “s” in “https://” is another marker – “s” stands for “secure!” In some browsers, either part or all of the URL bar will turn green. Users can also click on the lock icon to view the details of their connection to the site. It should state that the connection to the site is private and should allow a user to click through to advanced certificate information, including who the certificate is being issued by.
SSL’s Effect on SEO
Google has made a commitment to security on the internet. This extends not only to their own platforms like Search and Gmail, but also to the sites they display in their search results. The presence of “https” is now an official Google ranking signal. This means that websites using SSL security will rank higher in search engine displays. So besides the obvious benefits for your customers and trustworthiness, the SEO implications of using SSL are huge.
All of this makes SSL a pretty important addition to your website, but you should be wary of incorrect installation. As you’ve seen from the directions above, this is not a process that can be completed in a hurry. If you’re lost, checkout our HTTPS migration checklist or consult an agency or your own in-house developers for help.
In Conclusion
Secure Sockets Layer is an essential part of eCommerce today. Without this security, businesses leave themselves and their customers at the mercy of online hackers. We hear new stories about data breaches all the time – Target in 2013, eBay in 2014 and Ashley Madison in the summer of 2015 are three of the most famous.
It comes down to trust in the end. Marketing and sales efforts are all about bringing people in, gaining their trust and therefore, their business. So why shouldn’t an eCommerce website platform do the same?